LDAP Configuration
Jeff Duke
We use the Spring Security package ( Version 1.0.6 ). You can find the full configuration documentation here: Grails-Spring-Security-LDAP
Internal LDAP Settings
grails.plugins.springsecurity.ldap.authorities.retrieveGroupRoles = false
grails.plugins.springsecurity.ldap.authorities.retrieveDatabaseRoles = true
grails.plugins.springsecurity.ldap.useRememberMe = false
Below are some examples VetView LDAP configurations.
University of Georgia
VetView Configuration File:
grails.plugins.springsecurity.ldap.context.managerDn=<System Account>@uga.edu
grails.plugins.springsecurity.ldap.context.managerPassword=<password>
grails.plugins.springsecurity.ldap.context.server=ldaps://lds.uga.edu:636
grails.plugins.springsecurity.ldap.search.base=ou=users,o=uga
grails.plugins.springsecurity.ldap.search.filter=(cn={0})
grails.plugins.springsecurity.ldap.authenticator.dnPatterns=cn={0},ou=users,o=uga
grails.plugins.springsecurity.ldap.vetview.searchPattern={0}@uga.edu
Other Steps:
- Add Security Certificate into the Servers JVM
- ..\..\bin\Keytool -import -trustcacerts -keystore cacerts -storepass changeit -noprompt -alias InCommon -file c:\Certificates\InCommon_intermediate.cer
- ..\..\bin\keytool -import -trustcacerts -keystore cacerts -storepass changeit -noprompt -alias UserTrust -file c:\Certificates\UserTrust_root.cer
- Verify Correct JVM used on the Server
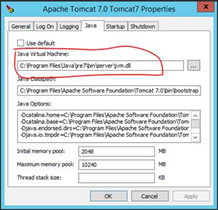
- Request a Firewall Exception between the Webserver and the LDAP server.
Auburn University
VetView Configuration File:
//Turn this switch on to enable Active Directory/LDAP Integration
grails.plugins.springsecurity.ldap.active = true
// In particular, the Admin Account is only required to located the full DN of the user within the search base.
// Once that's found you can just bind as the real user.
grails.plugins.springsecurity.ldap.context.managerDn = vvldap@vetmed.auburn.edu
grails.plugins.springsecurity.ldap.context.managerPassword = <password>
// User-specific LDAP Configuration
grails.plugins.springsecurity.ldap.context.server = ldap://dc.vetmed.auburn.edu:389/
grails.plugins.springsecurity.ldap.authorities.ignorePartialResultException = true
grails.plugins.springsecurity.ldap.search.base = OU=CVM_Users,DC=vetmed,DC=auburn,DC=edu
grails.plugins.springsecurity.ldap.search.filter = (sAMAccountName={0})
grails.plugins.springsecurity.ldap.search.searchSubtree = true
grails.plugins.springsecurity.ldap.auth.hideUserNotFoundExceptions = false
// enable group support
grails.plugins.springsecurity.ldap.authorities.retrieveGroupRoles = true
grails.plugins.springsecurity.ldap.authorities.groupSearchBase ='ou=*,dc=*,dc=*'
grails.plugins.springsecurity.ldap.authorities.groupSearchFilter = 'member={0}'
Other Information:
Cornell University
VetView Configuration File:
grails.plugins.springsecurity.ldap.context.managerDn=CN=VM-SVCVetViewAuth,OU=VM-ServiceAccounts,OU=HoldingIDs,OU=IDs,OU=VM,OU=DelegatedObjects,DC=cornell,DC=edu
grails.plugins.springsecurity.ldap.context.managerPassword=<password>
grails.plugins.springsecurity.ldap.context.server=<server address>
grails.plugins.springsecurity.ldap.search.base=OU=VM,OU=Staff,OU=NetIDs,OU=CUniv,DC=cornell,DC=edu
grails.plugins.springsecurity.ldap.search.filter=(uid={0})
Other Information:
The only difference in our setup then others is we combined the managerDN w/ the search base (I.e. where to start).
University of Minnesota
VetView Configuration File:
grails.plugins.springsecurity.ldap.context.managerDn=cn=<username>,ou=Organizations,o=University of Minnesota,c=US
grails.plugins.springsecurity.ldap.context.managerPassword=<password>
grails.plugins.springsecurity.ldap.context.server=ldaps://ldap-dsee.umn.edu:636
grails.plugins.springsecurity.ldap.search.base=ou=People,o=University of Minnesota,c=US
grails.plugins.springsecurity.ldap.search.filter=(cn={0})
Other Information:
Univserity of Missouri
VetView Configuration File:
grails.plugins.springsecurity.ldap.active=true
grails.plugins.springsecurity.ldap.context.managerDn=umcvetmedldap@missouri.edu
grails.plugins.springsecurity.ldap.context.managerPassword=<password>
grails.plugins.springsecurity.ldap.context.server = ldap://col.missouri.edu:3268/
grails.plugins.springsecurity.ldap.authorities.ignorePartialResultException = true
grails.plugins.springsecurity.ldap.search.base = DC=edu
grails.plugins.springsecurity.ldap.search.filter = (sAMAccountName={0})
grails.plugins.springsecurity.ldap.search.searchSubtree = true
grails.plugins.springsecurity.ldap.auth.hideUserNotFoundExceptions = false
Other Information:
There are multiple domains (UMC-USERS/col.missouri.edu for faculty and staff, and TIGERS/tig.mizzou.edu for students) so we point to the Global Address Catalog port 3268 instead of 636 and use a search base of DC=edu. The search filter is on sAMAccountName, so it’s looking for the AD username (MU calls it PawPrint).